Hackthebox.eu: how to register
Few days ago while attending the course “Practical Ethical Hacking – The Complete Course” by Heath Adams (aka The Cyber Mentor), in the section “Mid-course Capstone”, he introduced Hack The Box.
For those unfamiliar with it, Hack The Box is one of the most famous online platforms where you can experiment and improve your pentesting and cyber-security skills.
However, as explained during the video lesson, the “first step” that needs to be done in order to start using the virtual machines present in HTB is to “get yourself” the invitation code in order to register.
As you can see from the screen below, once you click on the button on the top right “Join Now” on the home page, you are redirected to the page that we have to “hack” in order to get the coupon which will then allow us to proceed with the actual registration process.
Although it is possible to find the solution to the problem simply by googling it, my opinion in this case is that “a good start is half the job”. Seriously, considering the type of portal we want to subscribe to, I think it’s essential to find the solution by ourselves.
Let’s start by analyzing what the console (i.e. errors, info messages) and the network (i.e. downloaded resources) tabs show us once we visit the page.
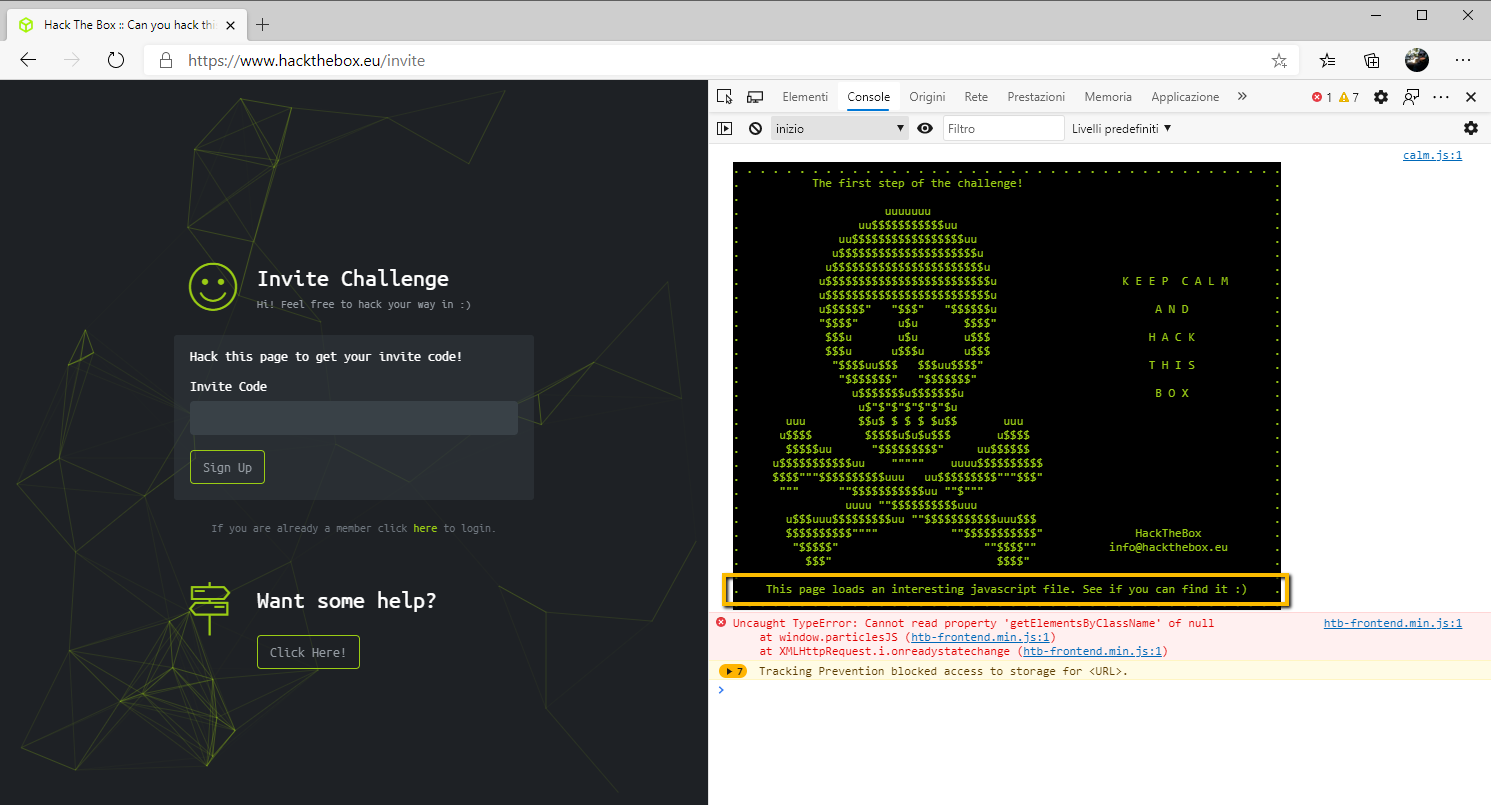
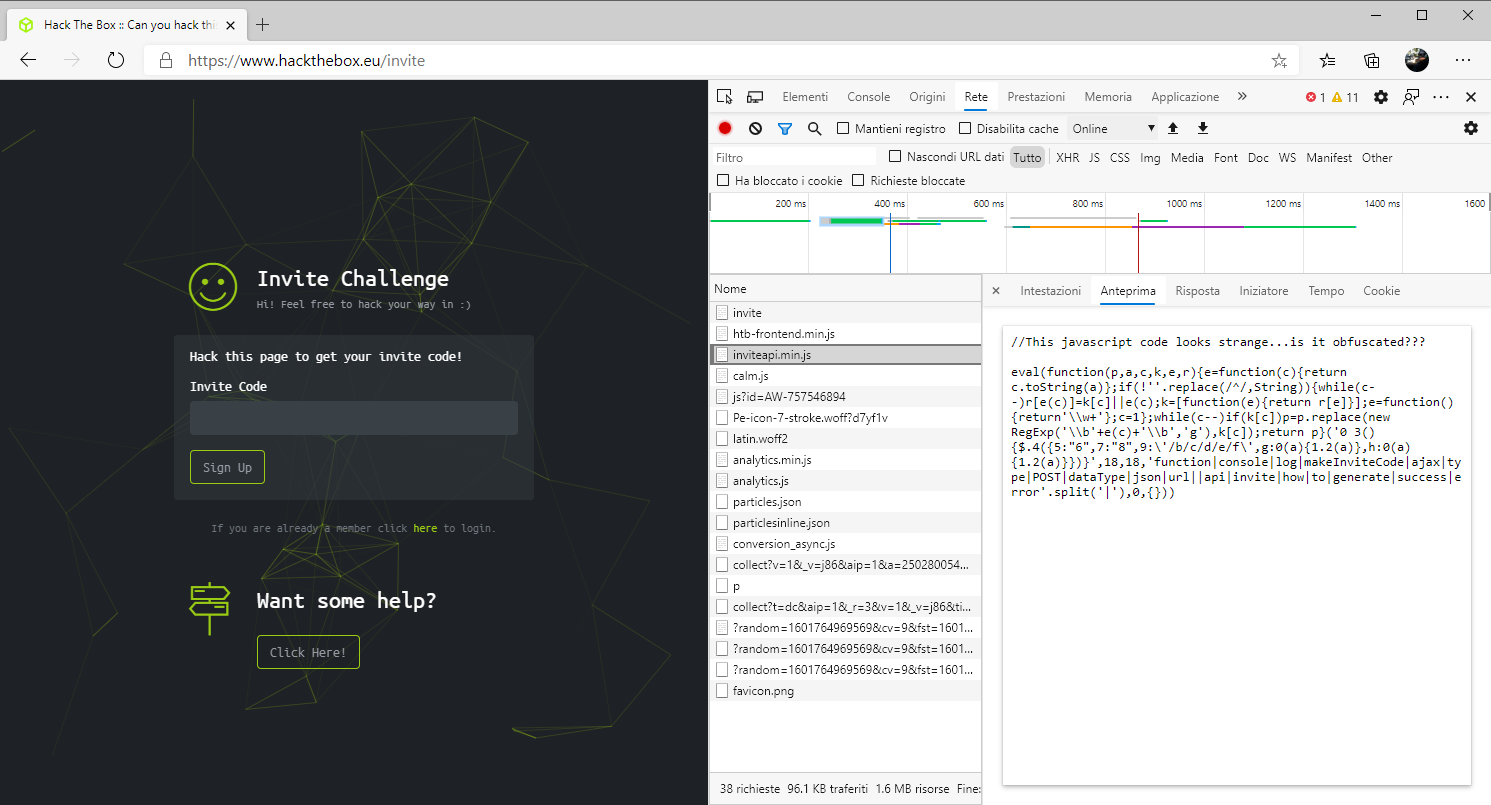
Among the listed files the most interesting one, from the name, it certainly seems to be inviteapi.min.js. This is a Javascript snippet which is obviously minified and obfuscated. Let’s convert our source file into something more human readable using one of the many available web resources (i.e JSNICE). We thus obtain the “clean” code for the Javascript function makeInviteCode().
'use strict';
/**
* @return {undefined}
*/
function makeInviteCode() {
$.ajax({
type : "POST",
dataType : "json",
url : "/api/invite/how/to/generate",
success : function(a) {
console.log(a);
},
error : function(a) {
console.log(a);
}
});
};
So let’s try to invoke this method directly from the Edge Webtools console and let’s use the printed information to try to decrypt the message.
NOTE: out of pure curiosity, I tried to invoke the function several times and as you can see from the screen it seems that the information shown in the data field can be obfuscated with the BASE64 or ROT13 algorithms.
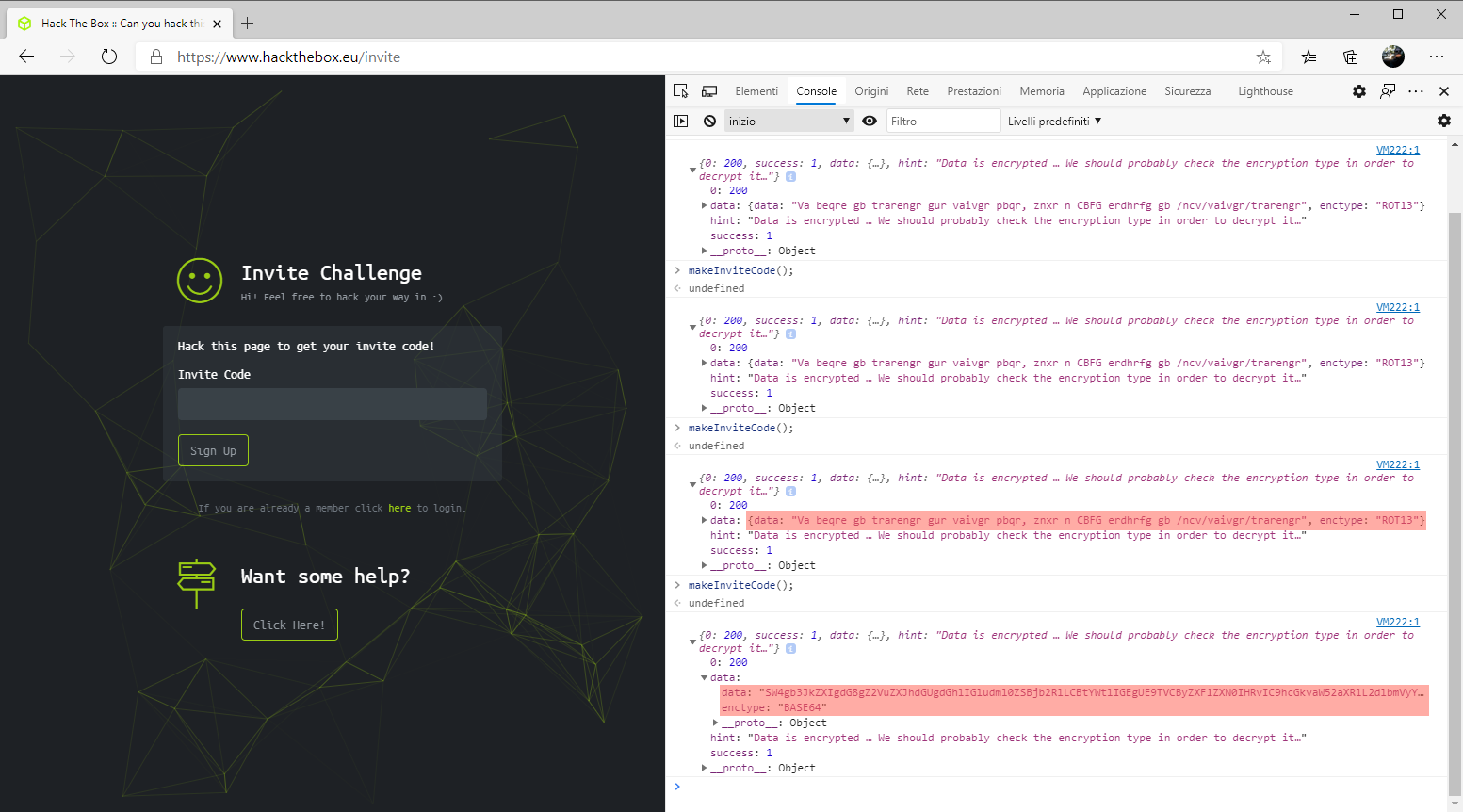
We just need to enter the encoded string and select the right algorithm in one of the many online services, such as this, to get the message :
In order to generate the invite code, make a POST request to /api/invite/generate
Let’s try to send the POST request as indicated. To do this, we can use a tool like curl or as in my case (I was in Windows) Powershell with the following command:
Invoke-WebRequest -UseBasicParsing "https://www.hackthebox.eu/api/invite/generate" -Method POST
Thus obtaining the answer as shown below:
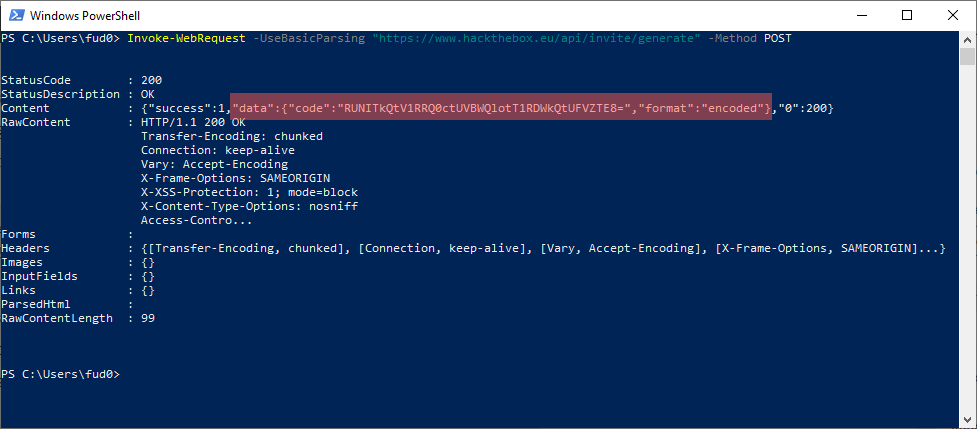
As indicated by that “encoded” our code is obfuscated in BASE64. Once the string has been decoded, we finally have our coupon code with which we can register at HTB.
Now you just have to start playing with their machines and experiment. Have fun!
